Cluster data centre (CDC) & private addressing (GCP) connection
When creating a GCP CDC through Instaclustr’s console, you can opt to choose broadcast private IP address at the Create Cluster/Add DC page.
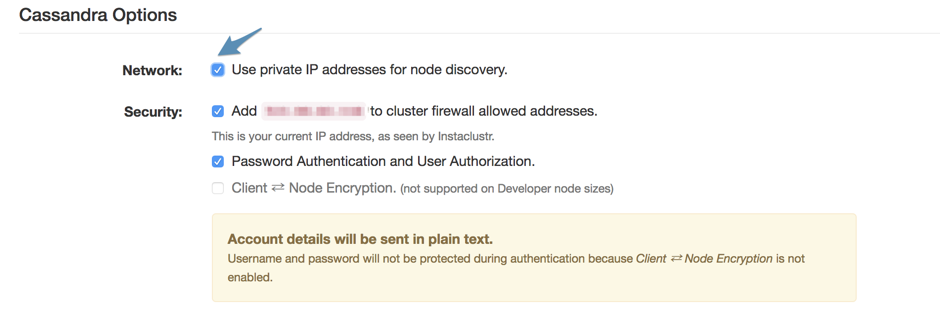
This allows for much more secure networking, but you will need access to the private network to be able to connect to the CDC.
Note: If you only intend to connect to your CDC privately, then choose broadcast private IP address when you create a new CDC. If you intend to connect both privately and from other sources then contact support for an explanation of the options and their implications.
There are 2 situations:
– The CDCs are provisioned in Instaclustr’s project. In this case, please contact Instaclustr Support on setting up a VPN tunnel. Please keep in mind that while the VPN is fully managed by Google, it requires a static IP on both ends. (Note: additional support charges may apply.)
– The CDCs are provisioned using a Run in your own account (RIYOA) setup. In this case, you have access to the network.
Table of Contents
Connecting to the cluster using a new instance
The steps to follow are:
1. Create a new virtual machine to connect to the cluster from the VM Instances page on the Google Cloud Console. You can install your app on this new machine and connect to the cluster using the available Cassandra drivers following the samples available on the Cluster Connection Info page. Make sure you launch it in the same network as the CDC you are interested in connecting to. You can add a new network from the VPC Networks Page
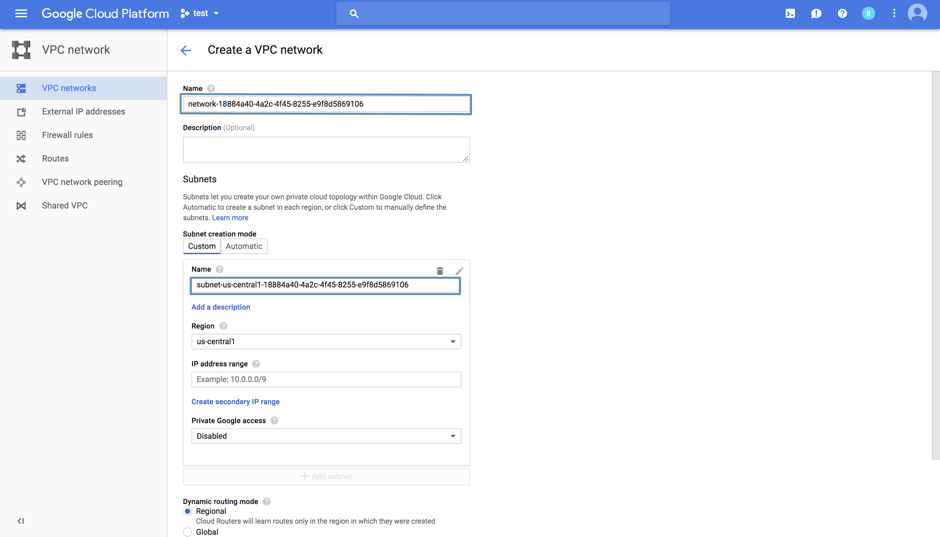
The Network will have the following nomenclature: network-<cdcID> and the Subnetwork will have the following nomenclature: subnet-<region>-<cdcID>. IP address range is the network range of the CDC, which can be found on the CDC details page.
Select the created network when creating a new network interface.
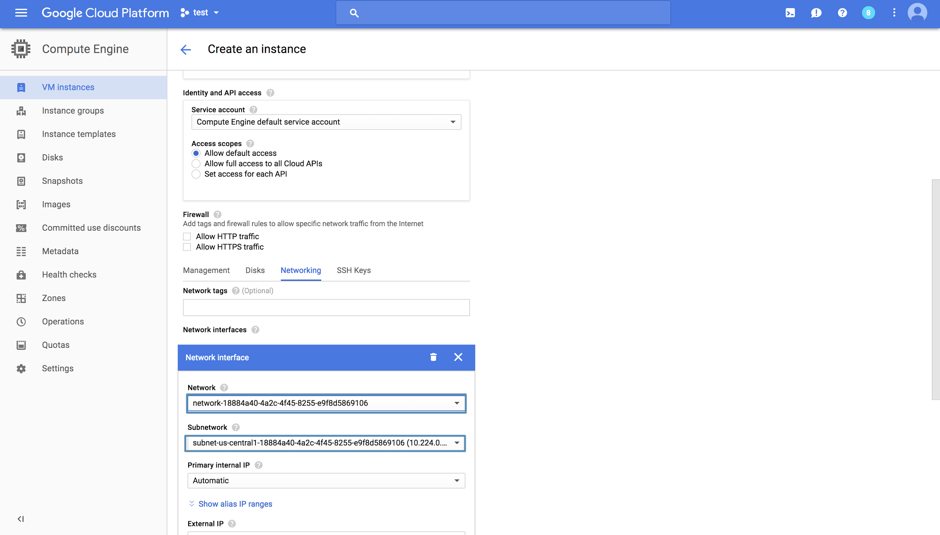
2. After you have created the virtual machine, you have to add a firewall rule to Cassandra to trust connections from the Internal IP of the VM. The Internal IP can be found on the VM instances page.
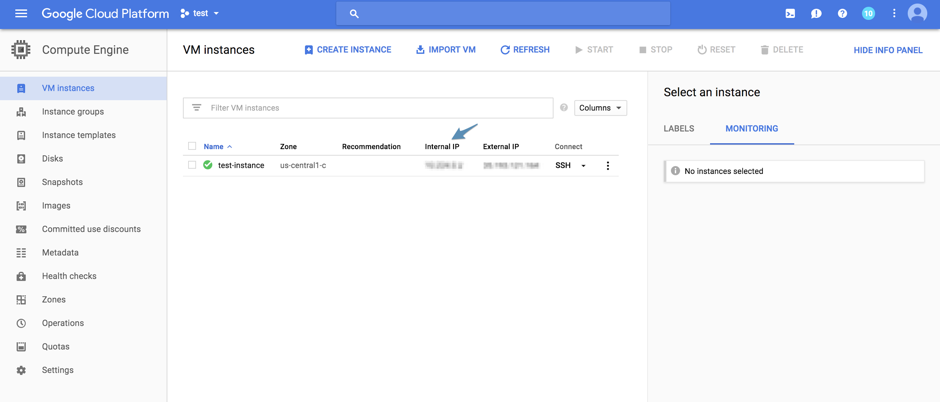
Add the Internal IP to the Firewall Rules under the Settings tab.
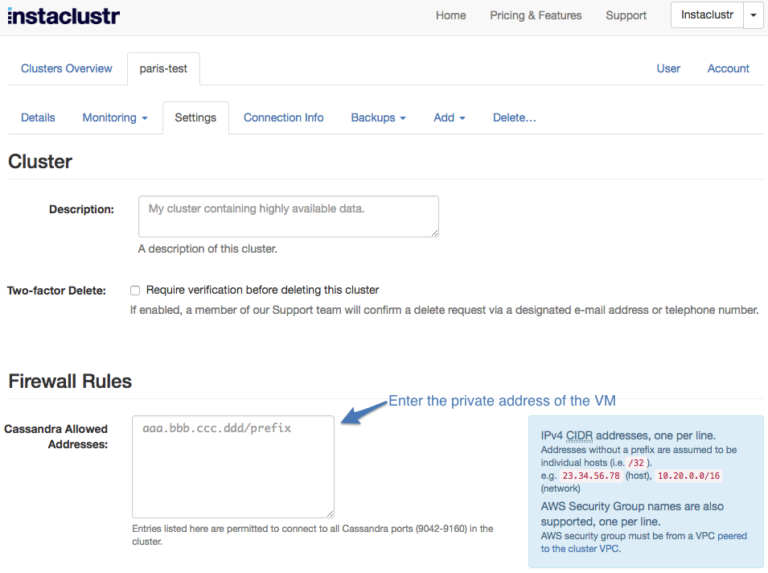
3. That’s it! You can test connectivity to the cluster by running the following commands:
nc -z <node_private_address> 9042; echo $?
- A result of 0 indicates success
telnet <node_private_address> 9042
- A telnet prompt indicates success, enter quit to close the connection.
Connecting to the cluster using an existing app on GCP
If you already have an existing application you would like to use to connect to a CDC with private address broadcasting, you will have to setup a VPN tunnel. Doing this requires two static external IP addresses. Additionally, the CIDR range of the network must not conflict with the CIDR ranges of the networks on the peer side of the VPN.
1. Head over to the VPN subtab of the Interconnect tab under the Networking menu from the Google Cloud console and create a VPN connection. Associate the VPN with the network and region of your CDC. Note that for the IP address, you have to assign it a static IP, which will be the IP of your VPN.
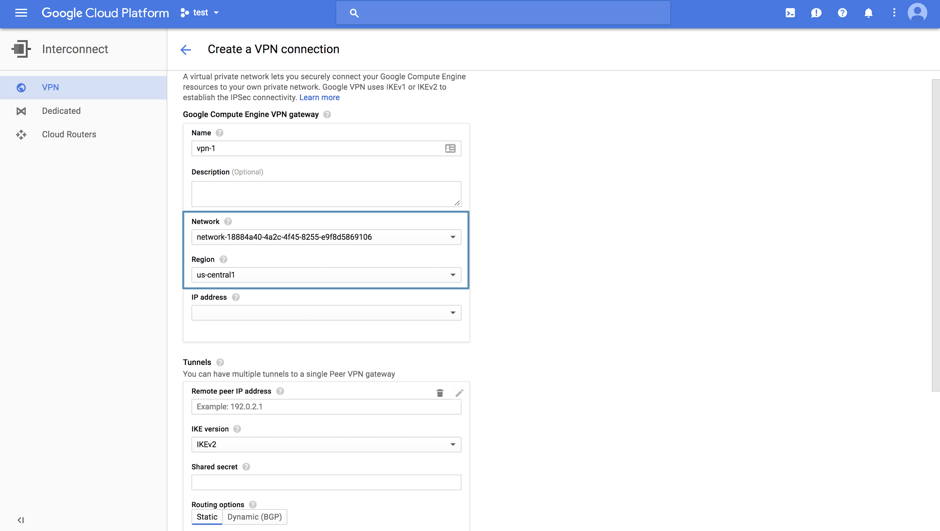
Repeat this process, but this time for your app.
2. This is the part where you actually create the tunnel. Provide the remote VPN IP for each of the VPNs, and give a shared secret that is the same for both the VPNs. For the remote network IP range, specify the CIDR of your remote. You can also specify the local subnetworks for extra performance gain.
For example, suppose I had 2 CDCs, 1 in 10.0.0.0/18 with VPN IP 104.196.162.188 (which we’ll call VPN-A) and the other in 10.224.0.0/12 with VPN IP 104.198.7.116 (which we’ll call VPN-B). Then while adding the tunnel, for VPN-A, we’ll have to specify remote peer IP as 104.198.7.116 and remote network IP range as 10.224.0.0/12. This is reversed while adding the tunnel for VPN-B. In either case, the shared secret has to be the same string for both the VPNs.
3. Add the corresponding network to the Firewall Rules allowed for your cluster. You don’t have to add a route which routes traffic headed for the peer VPN’s CIDR to the VPN because they are added for you when you create the VPN tunnel. This completes the setup, and you can test the connectivity using your application.