How Clients Connect to a PostgreSQL Cluster Using Azure Private Link connection
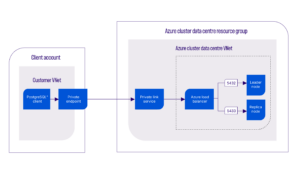
In Azure Private Link architecture, the PostgreSQL cluster must be configured as a private network cluster. To route traffic properly, an Azure Load Balancer is configured with multiple rules for different types of requests: read-write on port 5432 and read-only on port 5433.
Clients must connect using a Private Endpoint, which ensures that the connection remains private by routing traffic through the Microsoft backbone network instead of the public internet. Access to the Private Link service is managed through Azure Role-based Access Controls or subscriptions to ensure appropriate permissions.
Step-by-Step Connection Flow:
- Client Connection through Azure Private Endpoint
- Clients must initiate a connection from the Private Endpoint to Azure Private Link service. Depending on the access visibility settings mentioned above, the connection might be approved automatically or require clients to manually approve through Azure Portal.
- The fully qualified domain name (FQDN) (if DNS setting is configured) resolves to the private IP address of the Private Endpoint, and then forwards traffic to the Private Link service over the Microsoft backbone network.
- Traffic stays within Microsoft’s private network, ensuring secure connectivity.
- Routing through Private Link Service and Load Balancer
- The Private Link service forwards the request to the Azure Load Balancer.
- The Load Balancer determines the appropriate traffic type:
- Port 5432: For read-write requests
- Port 5433: For read-only requests
- Based on the port, the Load Balancer routes the traffic to the correct target group (read-write -> leader node, read-only -> replica nodes).
Questions
Please contact Instaclustr Support for further assistance.