Single Sign On (SSO)
Instaclustr Account Owners can enable single sign-on (SSO) as an extra layer of security for their Instaclustr accounts through SAML 2.0-based authentication. This allows Instaclustr users in an SSO enabled account to sign in with existing credentials which have been registered with an Identity Provider (IdP) configured against the account instead of maintaining a separate username and password for Instaclustr. SSO allows account owners to easily manage and control users access from a centralized location.
Please contact [email protected] to discuss enabling SSO for your account.
Table of Contents
Features
- SSO via a SAML 2.0 compatible Identity Provider of your choice
- User provisioning and management with SCIM 2.0
Key Benefits
- By integrating with your enterprise Identity Provider you can:
- Store user credentials on a trusted service of your choice
- Centralize access and user management
- Convenience – No need to register users individually through the sign up page
- Choose an Identity Provider to meet your specific security requirements
Requirements for SSO Integration
You must meet the following requirements to be eligible for SSO integration with Instaclustr:
- An Identity Provider which supports SAML 2.0.
- We will require the following information from your SAML 2.0 application:
- Identity provider Issuer URI
- Single Sign-On URL
- X.509 Signature Certificate
- A SCIM (System for Cross-domain Identity Management) 2.0 application is required to manage SSO users.
- Instaclustr’s SCIM 2.0 API supports the Basic and Bearer Authentication schemes.
Additional requirements for Azure AD:
- Azure AD Premium P1 (minimum)
- This is required to manage User -> Account membership through SCIM 2.0, as the premium plan allows adding groups to an application in Azure AD.
- Without this, it is still possible to provision users, but they will need to be manually assigned to an account once they have been provisioned.
Examples of Identity Providers we support are Okta and Azure AD.
Overview of the SSO enablement process
To begin the process of enabling SSO for your account, raise a support ticket with Instaclustr at [email protected].
Once the request to enable SSO has been approved, log in to the Instaclustr console and navigate to Account → Manage Users → SSO.
Upon completion of the SSO enablement request form, Instaclustr will lodge a follow up support request and return the following information so you may configure the SAML 2.0 application on your Identity Provider:
- Assertion Consumer Service (ACS) URL
- Audience URI
- Relay State
- SAML attribute requirements
A summary of the SSO enablement process is as follows:
-
Establish trust between Identity Providers by exchanging the SAML 2.0 details using the SSO enablement request form.
- An SSO enabled test account will be created and shared with the requestor. This test account will be linked to the previously registered Identity Provider.
-
Testing the SCIM 2.0 integration and verifying that user provisioning, de-provisioning and SCIM group assignment works as expected. Click here to see more details.
- Verifying that the Identity Provider and Service Provider initiated SSO login flows work as expected. Click here to see more details.
-
Migratory tasks to be performed by the requestor and Instaclustr in preparation for enabling SSO on the production account(s).
- Instaclustr will enable SSO on the requested account(s) at an agreed upon time.
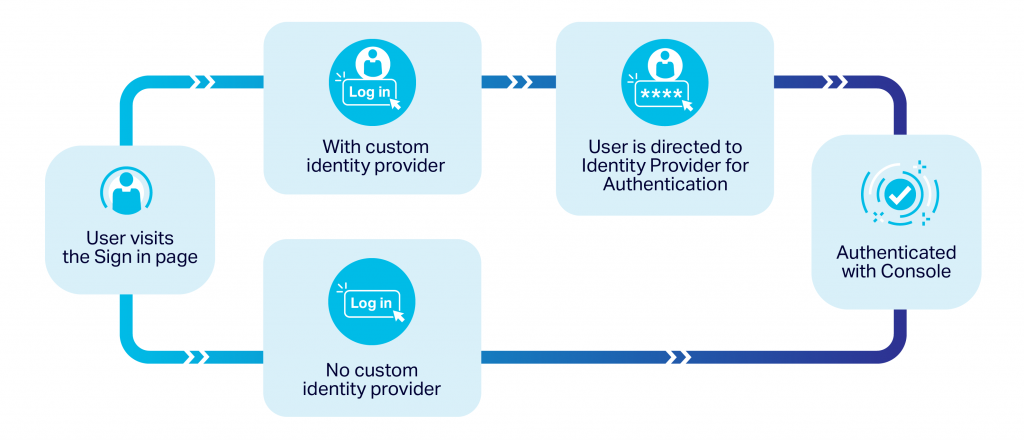
Instaclustr limits each account to only one Identity Provider. After enabling SSO on an Instaclustr account, all non-Owner users will be directed to the configured Identity Provider login for authentication when attempting to log in through the Instaclustr console. Any user created before enablement must be created on the configured Identity Provider to ensure continued access.
If you would like to disable SSO on your account for any reason, the Account Owner will need to raise a support ticket with Instaclustr at [email protected]
Testing SCIM 2.0 integration with Instaclustr
After providing Instaclustr with your SAML metadata information through the SSO enablement request form, an invitation to an SSO enabled test account will be shared you. The following must be done to complete the testing phase –
- Accept the invitation to the test account. You may invite other members of your company to this account as an Owner if they need to be involved in the testing process.
- Generate the User Management API key on the test account. The API key may be generated by navigating to Account → API Keys.
- Create the SCIM 2.0 application on your Identity Provider using the User Management API Key and username with the Basic Authentication scheme.
- Verify that your SCIM 2.0 application has retrieved the SCIM groups. Note that the SCIM groups represent Instaclustr Accounts.
- Provision a user with the SCIM 2.0 application and link the user to the SCIM group representing the test account.
- Verify that the user has been added to the test account by navigating to Account → Manage Users → Linked Users.
Testing SSO login with Instaclustr
After provisioning a user with the SCIM 2.0 application, you may now test SSO login as follows –
- Assign the Instaclustr SAML application to the test user.
- Verify that the Identity Provider initiated login is successful.
- Verify the Service Provided initiated login is successful – when the user attempts to log in from the console, they are redirected to your registered Identity Provider and gain access to the console on successful login.
Reviewing Roles for SSO
To prepare for SSO integration on an account, it is advised to review permissions of the existing users on the account and consider the following information as part of the pre-planning process:
- SSO is enabled on an Instaclustr Account level. When enabled, all users in the account will be required to log in through the registered Identity Provider. The exception to this are:
- Account Owners, who may access the console through the regular Instaclustr login mechanism, or use the Identity Provider initiated login.
- Users who have signed up through Google – who may either log in through Google, or through the registered Identity Provider.
-
- It is recommended for SSO enabled accounts to have no more than 2 Owners. 1 Owner should be a service account and the other can be a real user. The service account may be used to generate the User Management API key that is used for SCIM. It is recommended to have as few Owners as possible and assign appropriate roles to the remaining users on the account.
What to Expect Once SSO is Enabled
Once your account has been bound to your Identity Provider and SSO enabled –
- For users who have not signed up through Google –
- All non-Owner users linked to the account will be required to authenticate using SSO and will no longer be able to authenticate using their Instaclustr password. A non-Owner user can initiate authentication either via the Instaclustr console or via your Identity Provider’s console (if supported).
- Owner level users on the other hand will continue to authenticate using their Instaclustr password when logging in through the Instaclustr console, but also have the option to authenticate through the Identity Provider initiated login flow.
- For users who have signed up through Google –
- All users who have signed up through Google will continue to be able to use Google sign-in.
- Non-Owner users may either log in through –
- Google sign-in, or
- The Service Provider initiated login flow with the registered Identity Provider if the user manually enter’s their username or e-mail address on the login page, or
- The Identity Provider initiated login flow with the registered Identity Provider.
- Owner level users may either log in through Google sign-in or through the Identity Provider initiated login flow with the registered Identity Provider.
Managing SSO Users with the User Management API
Instaclustr provides a User Management API for SSO-enabled accounts which uses the System for Cross-domain Identity Management (SCIM) standard. This API allows users to be provisioned and deactivated in Instaclustr accounts that have SSO enabled. It is important to note that when you enable SSO on your Instaclustr account, the user management API becomes the default method for managing users on the account. The existing user management tools on the Instaclustr console will remain active, however, these are not recommended and should only be used after consulting with Instaclustr support as it may cause user synchronization issues. For more information on the use of the User Management API, click here to see our API documentation.
Limitations
SSO integration with Instaclustr does not support the following features:
- Just-In-Time user provisioning
- The SCIM group API is limited to account retrieval and membership operations. Account provisioning, modification and deletion are not supported.
- Only 1 account should be used to generate the User Management API Key per organization. Cross management of users with API keys from multiple accounts is not supported.