Adding a KMS Key for use on the Instaclustr Platform using AWS Run in Your Own Account (RIYOA) Provisioning
Instaclustr supports the creation of clusters in your own cloud provider account, which has EBS and S3 storage encrypted at rest using customer supplied KMS Keys. These instructions outline how to create the KMS Keys, and add them to the Instaclustr Platform.
- Creation of KMS Keys and Setup of IAM Permissions
The information on how to setup and configure KMS Keys for usage on RIYOA provisioning is outlined in the Instaclustr Run In Your Own Account AWS Provisioning Setup Guide, which is provided as part of your RIYOA onboarding. If you do not have a copy of this document please reach out to Instaclustr Support.
Once you have configured the key in your AWS account, go to the Instaclustr console,
- Navigate to Cluster Resources -> Encryption Keys by clicking on the gear icon at the top right hand corner.

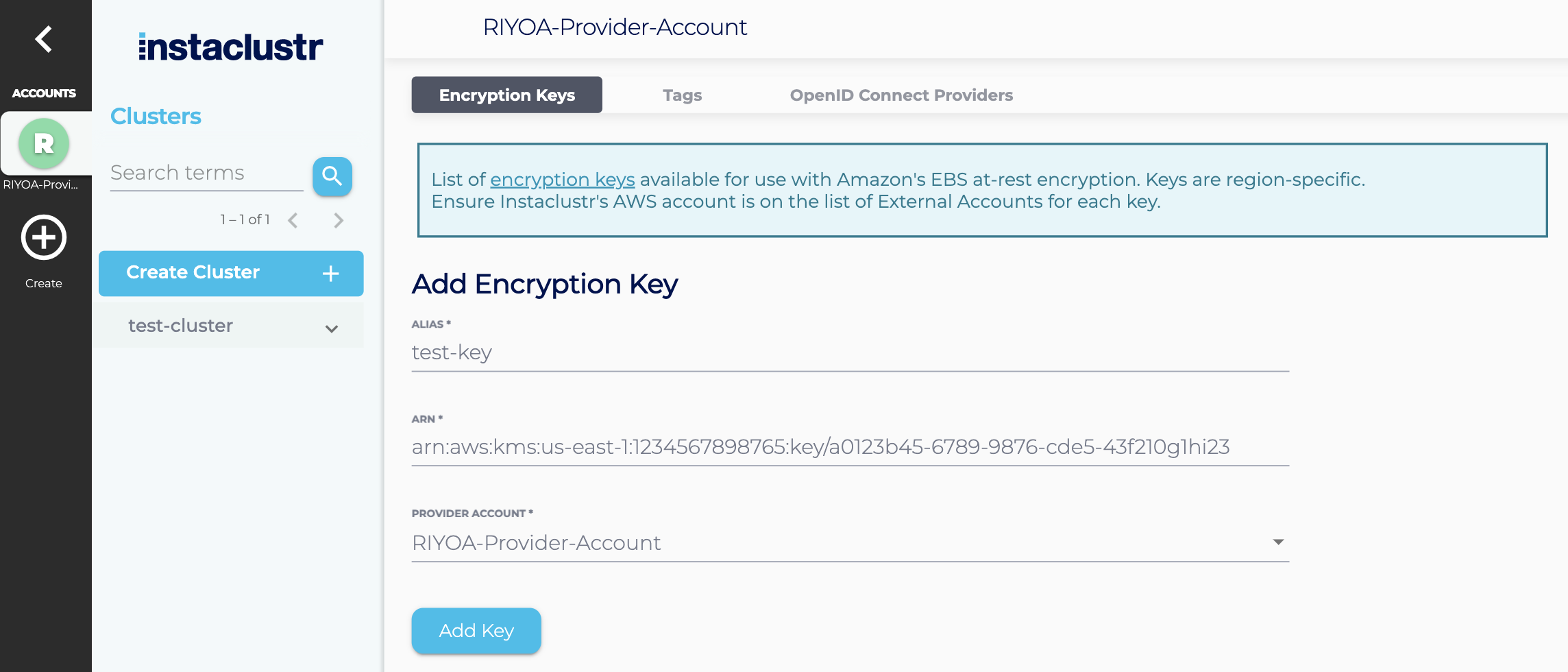
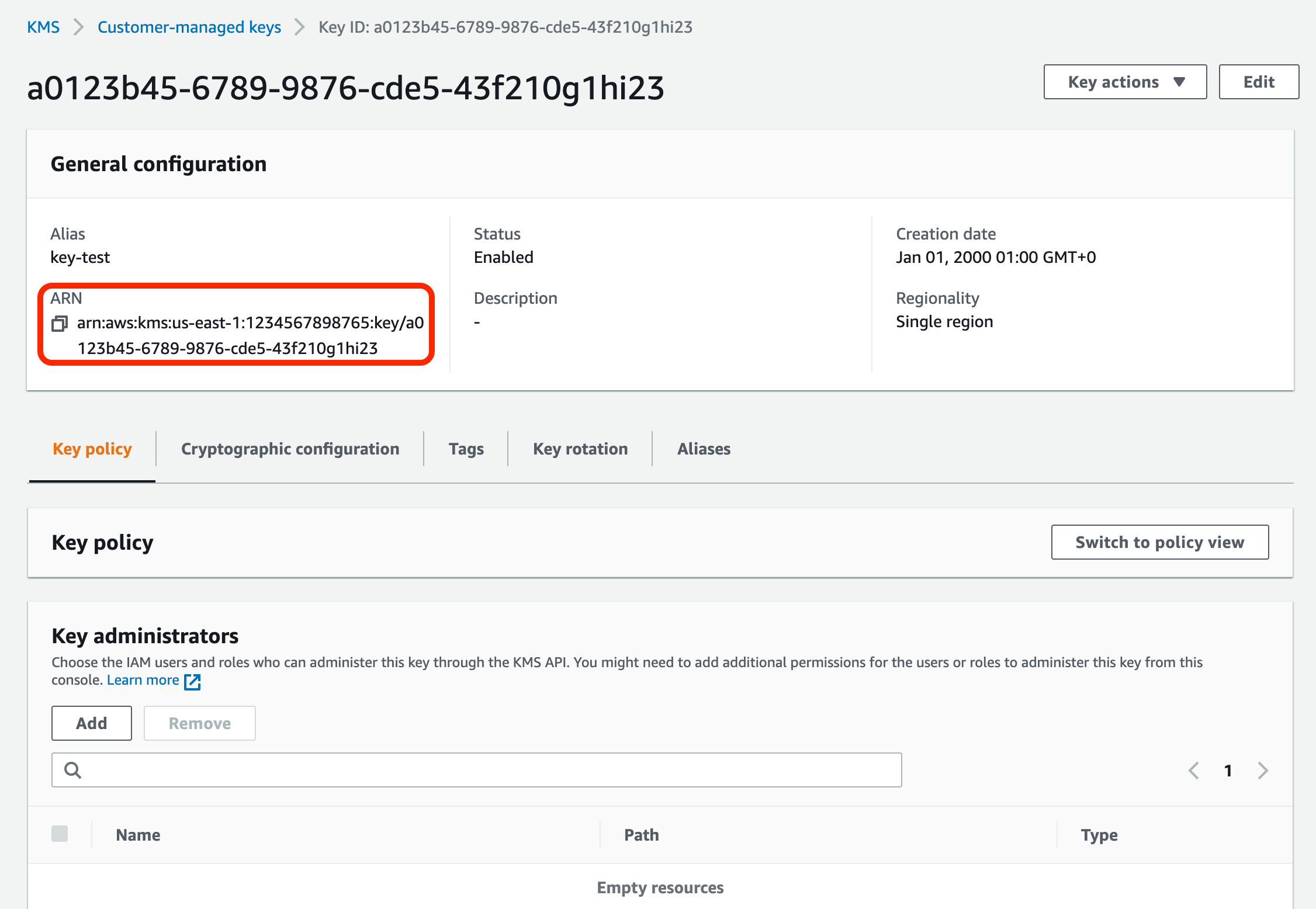
- You’ll need the AWS key’s ARN, found in the key’s details after key creation.
- The alias will identify this key in other parts of the Instaclustr console. Add the alias for your key, the AWS key’s ARN, and set the Provider Account to the provider account that has been setup for this key. For RIYOA provisioning – this is not the “Instaclustr” Provider Account. Once you have done this, click on Add Key to add the key to your account.

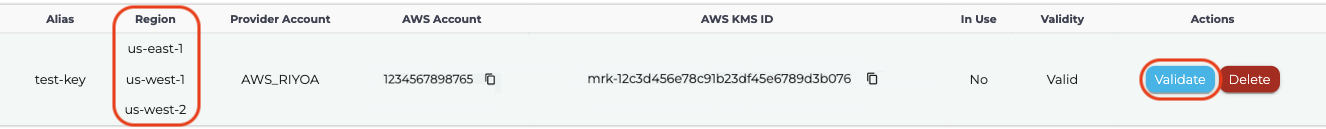
- Once the key is successfully added to the Instaclustr Console, it will appear in the table.
- Use the Validate button to check the validity of the key before cluster creation. For Multi-Region keys, the Validate button updates the list of regions that key is available in.

- When you Create a Cluster or Add a Data Centre to an existing cluster, you will now have the option to enable EBS encryption.
Note: For Multi-Region keys, when a key is replicated in another region, the ARN of the replica region must be added to the allowed resources on Instaclustr’s provisioning IAM policy, to be able to use the key in the new region. This must be done for all regions where the key is replicated.
For more information regarding Amazon’s encryption service see:
- Share Custom Encryption Keys More Securely Between Accounts by Using AWS Key Management Service
- Amazon EBS Encryption
- Multi-Region keys in AWS KMS
Further Questions
We are available to provide additional information and guide you through this process. Please contact Instaclustr Support or raise a new ticket.
 By Instaclustr Support
By Instaclustr Support