Managing Apache Kafka Users
Instaclustr provides both a User Management UI and User Management API for Kafka clusters to help you with managing users. The User Management UI and API provide four functions:
- List Users
- Add Users
- Change User Passwords
- Delete Users
All Kafka users created or listed in the Users list will have read and write access to all topics in the cluster. There are details below on how to change this in Kafka ACL Management. If you require any other configuration, please submit a support request.
All Kafka clusters will have an ickafka user automatically created as a convenience, which can be deleted. If the ickafka user is deleted or has the password changed the new password will not be stored and the credentials will disappear from the cluster’s Connection Info page. Because changed passwords and new user passwords will not be stored, ensure you make a note of the passwords to user accounts.
For Kafka Schema Registry and Kafka Rest Proxy services, the user password can be updated from the dashboard Kafka user management UI. We do not support user deletion or creation for these services. Make sure you take into account that the services will be restarted when actioning a password change.
User Management UI
These examples show how to use the features of the Instaclustr console’s User Management UI.
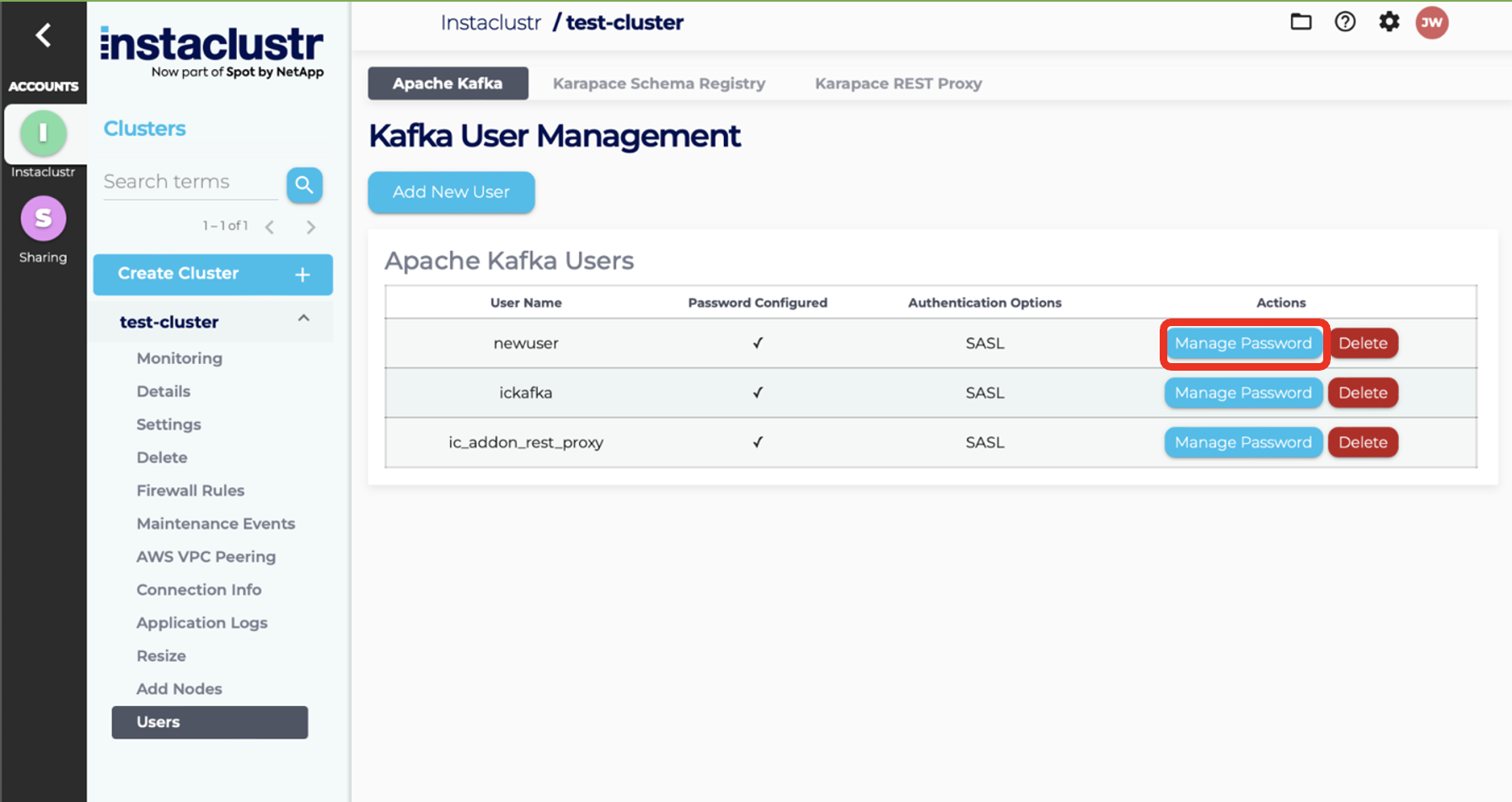
List Users
- To list available Kafka users, navigate to the Users tab of your Kafka cluster.
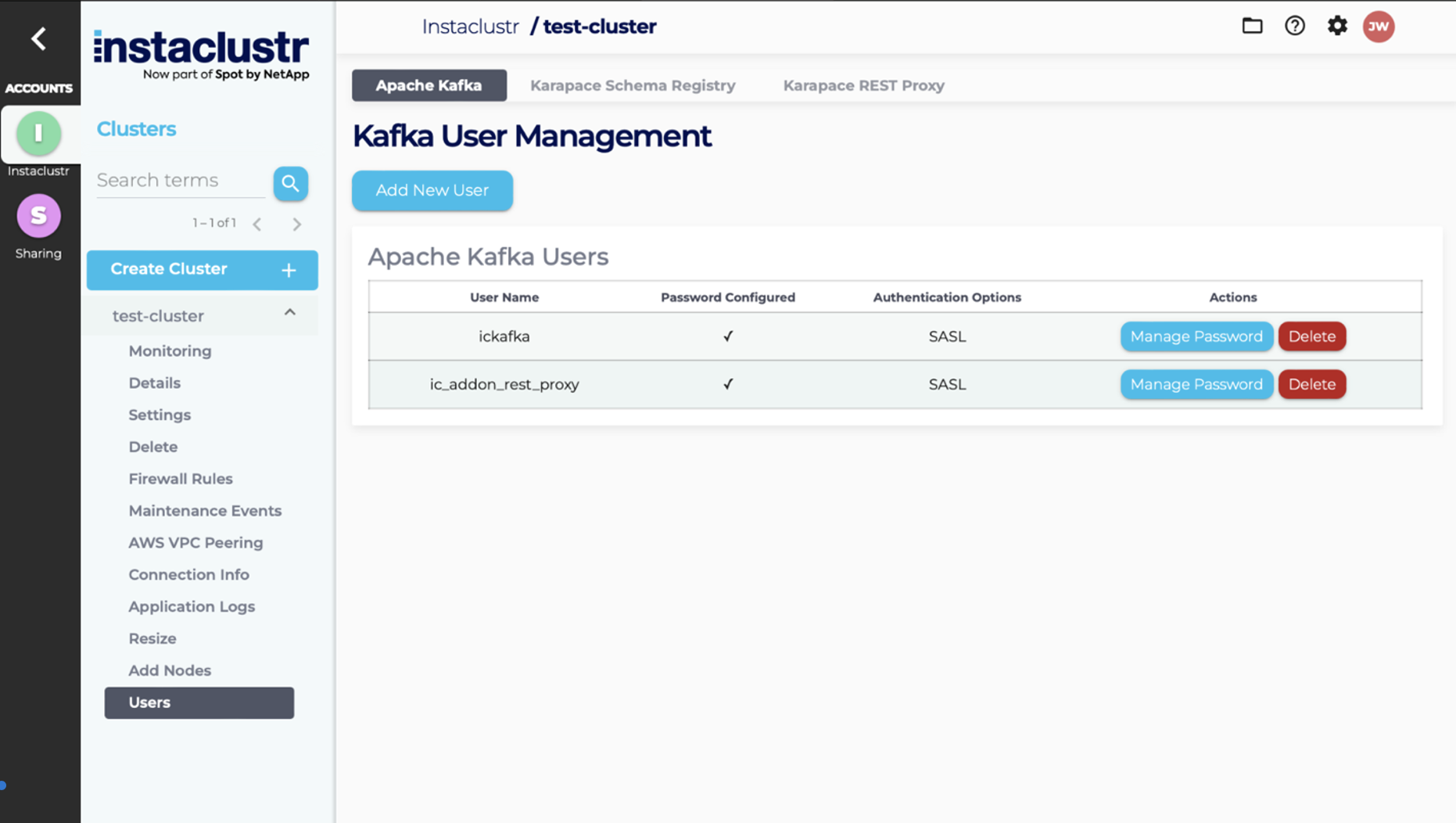
- The Users page will list all Kafka users on the cluster. If you have enabled Kafka Schema Registry and/or Kafka Rest Proxy, you will be able to see the default users for those services by clicking on the relevant tabs at the top of the page.
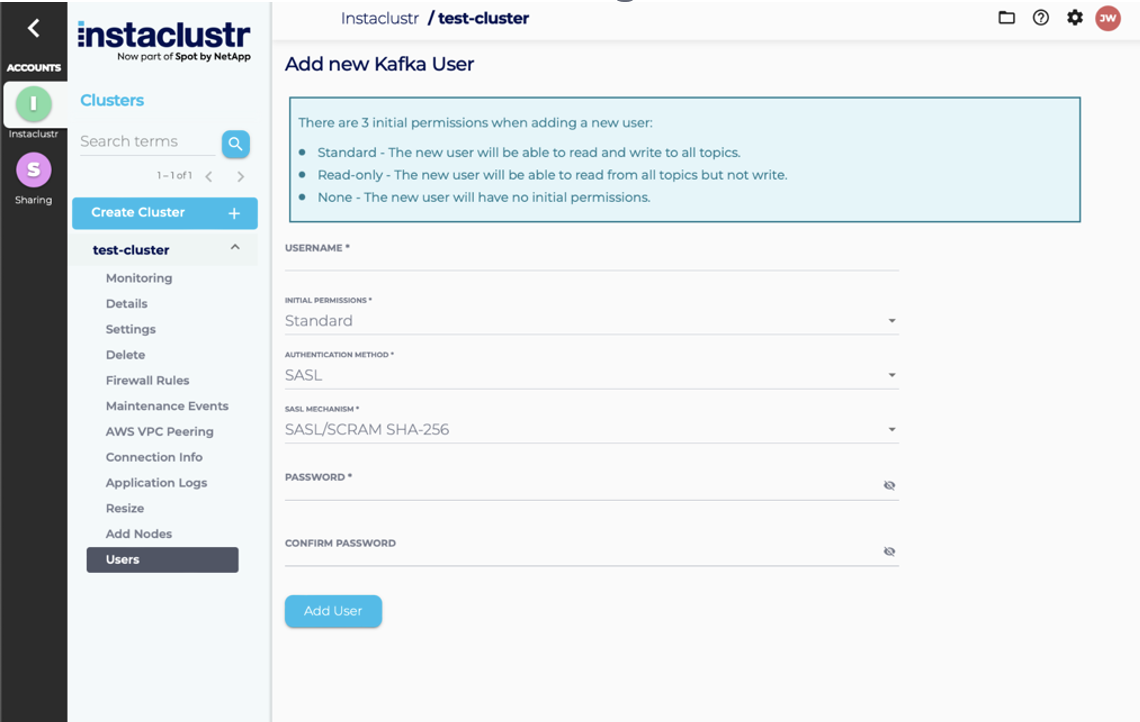
Add User
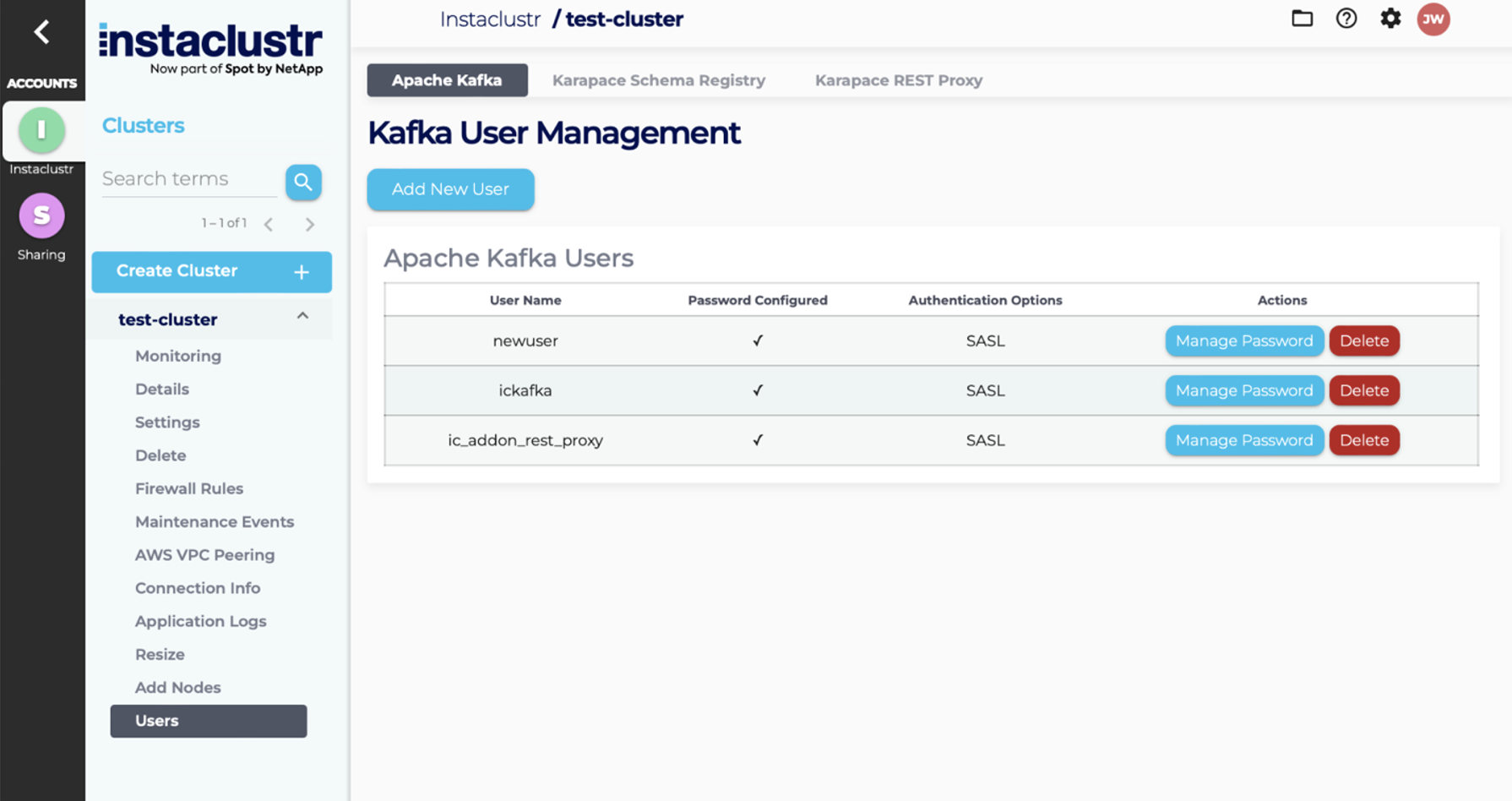
- To add a new Kafka user, first, navigate to the Users page of your Kafka cluster. From the Users page, click the Add New User button. You will be redirected to the form for adding a new user.

- Enter the desired username and password for the new Kafka user, the desired level of initial permissions, and a user authentication mechanism. The default user authentication mechanism is SASL, a method of password authentication. For MTLS enabled clusters you will also have the option of MTLS authentication, a certificate based mechanism. To configure see Managing Certificates on a mTLS cluster. The initial permissions setting can be one of three things:
- Standard – The new user will be able to read and write to all topics
- Read-only – The new user will be able to read from all topics, but not write
- None – The new user will have no initial permissions
- Once you’ve entered the required information, click the Add User button. This will create the new user and redirect you to the Users page, where the new user will be shown in the list of users.
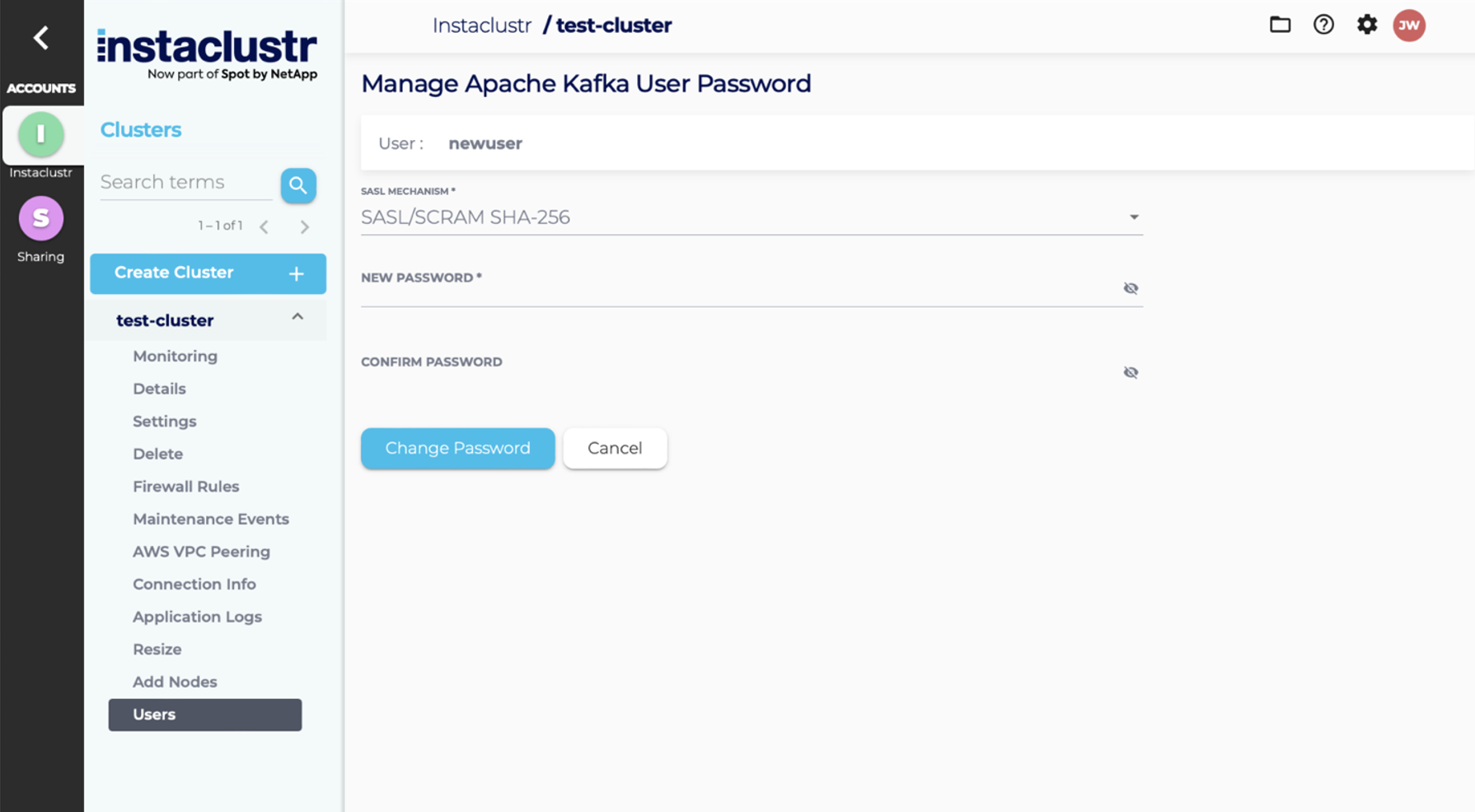
Manage User Password
- To change the password of an existing Kafka user, first, navigate to the Users page of your Kafka cluster. From the Users page, click the Manage Password button of the user whose password you want to change. You will be redirected to the form for managing your password.

- Enter a new password for the user and a user authentication mechanism. Once you’ve entered the required information, click the Change Password button.

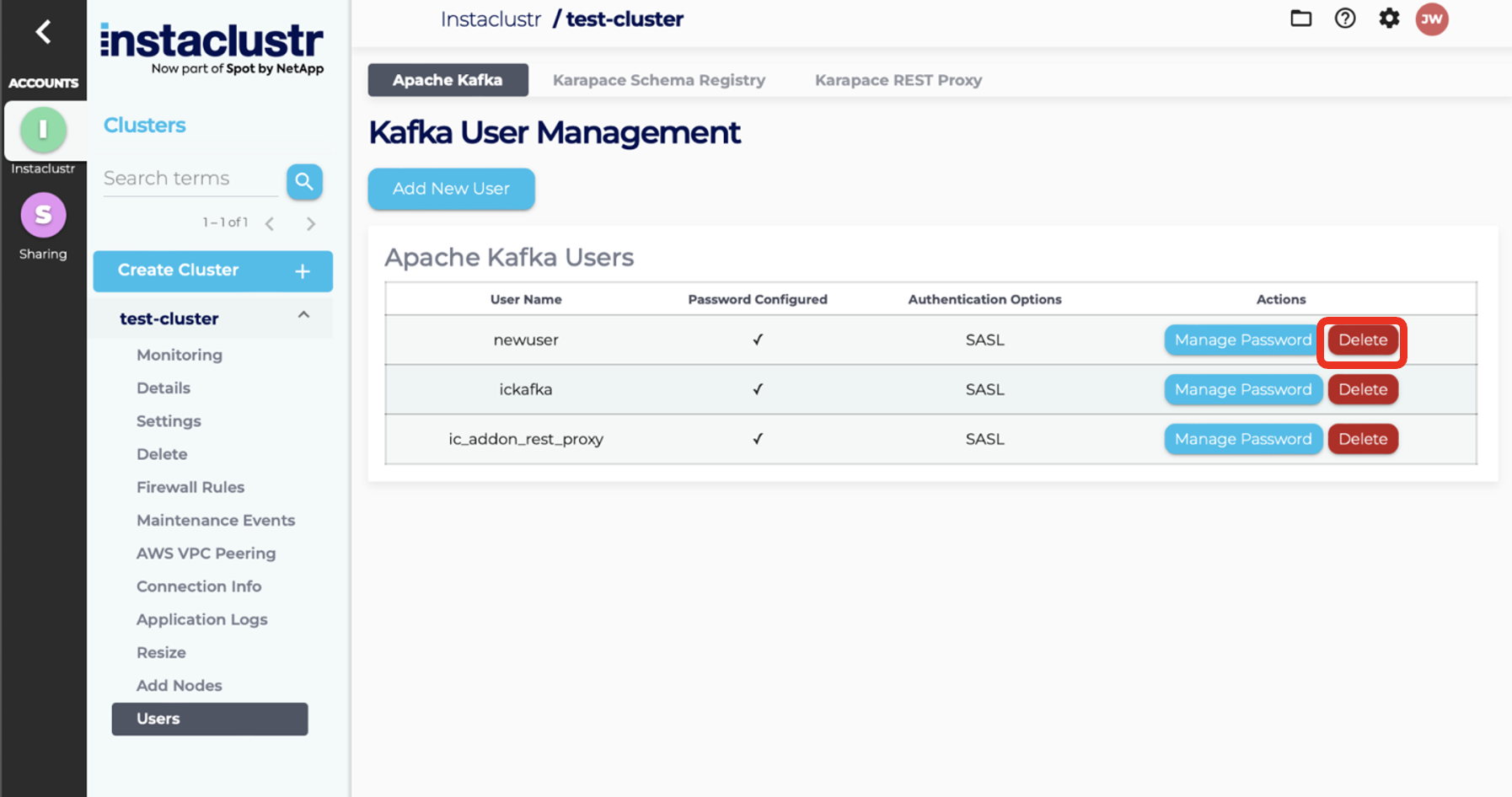
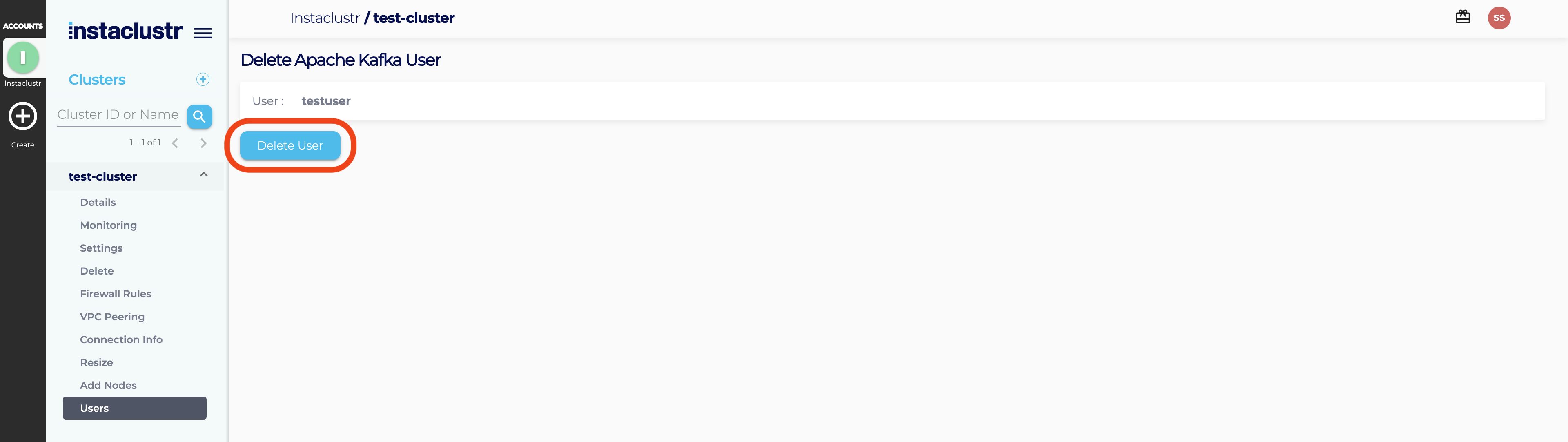
Delete User
- To delete an existing Kafka user, first, navigate to the Users page of your Kafka cluster. From the Users page, click the Delete button for the user that you want to delete.

- Click on the Delete User button to confirm the deletion of the user.

User Management API
For examples on how to access these features using the Instaclustr User Management API please refer to our API Documentation.
To provide customers with a high level of security, the Kafka User API endpoint will not store or allow customers to retrieve passwords for Kafka users. Therefore, these passwords should be securely stored.
Please note that the Kafka Enterprise Addons do not currently support add user or delete user functions. This includes:
- Kafka Schema Registry,
- Kafka Rest Proxy,
- Karapace Schema Registry
- Karapace Rest Proxy
 By Instaclustr Support
By Instaclustr Support